The implementation of ID verification to Twitter (now known as X) is something that’s been long rumored ever since Elon Musk bought the platform. This new security feature may be coming soon as details on how the verification process will work have recently emerged.
At least potentially.
This information comes from independent app researcher Nima Owji who shared a screenshot of an in-app window revealing some of the materials Premium users will need to verify their identity. They include a government-issued ID plus a device with a working, uncovered camera – presumably a smartphone. Verification is said to take about five minutes or so. The message also tells people to “be prepared to take a sefie and photos of your ID.” We assume “sefie” is a typo and the platform meant to say “selfie” instead. As you can probably guess, this is still a work in progress; although the fact this message appeared hints at an imminent launch.
#X keeps working on the ID verification. You should upload a photo of your ID and take a live selfie. https://t.co/3bdGgzlnZh pic.twitter.com/F4ssglakHRAugust 16, 2023
Important context
Looking at the fine print, X will store images of your ID as well as your biometric data on its servers for up to 30 days. During that time, the platform will share your information with identity verification company Au10tix “for the purpose of confirming [your] identity.” Additionally, X will use your data for “safety and security” reasons.
Doing a quick Google search on Au10tix, it looks like the company has a pretty clean rap sheet. It hasn’t had any public data breaches. On the surface, it appears Elon Musk made a good choice in picking Au10tix as a third-party partner. Although given all the controversies that have come as a result of Musk’s decisions, we will remain skeptical.
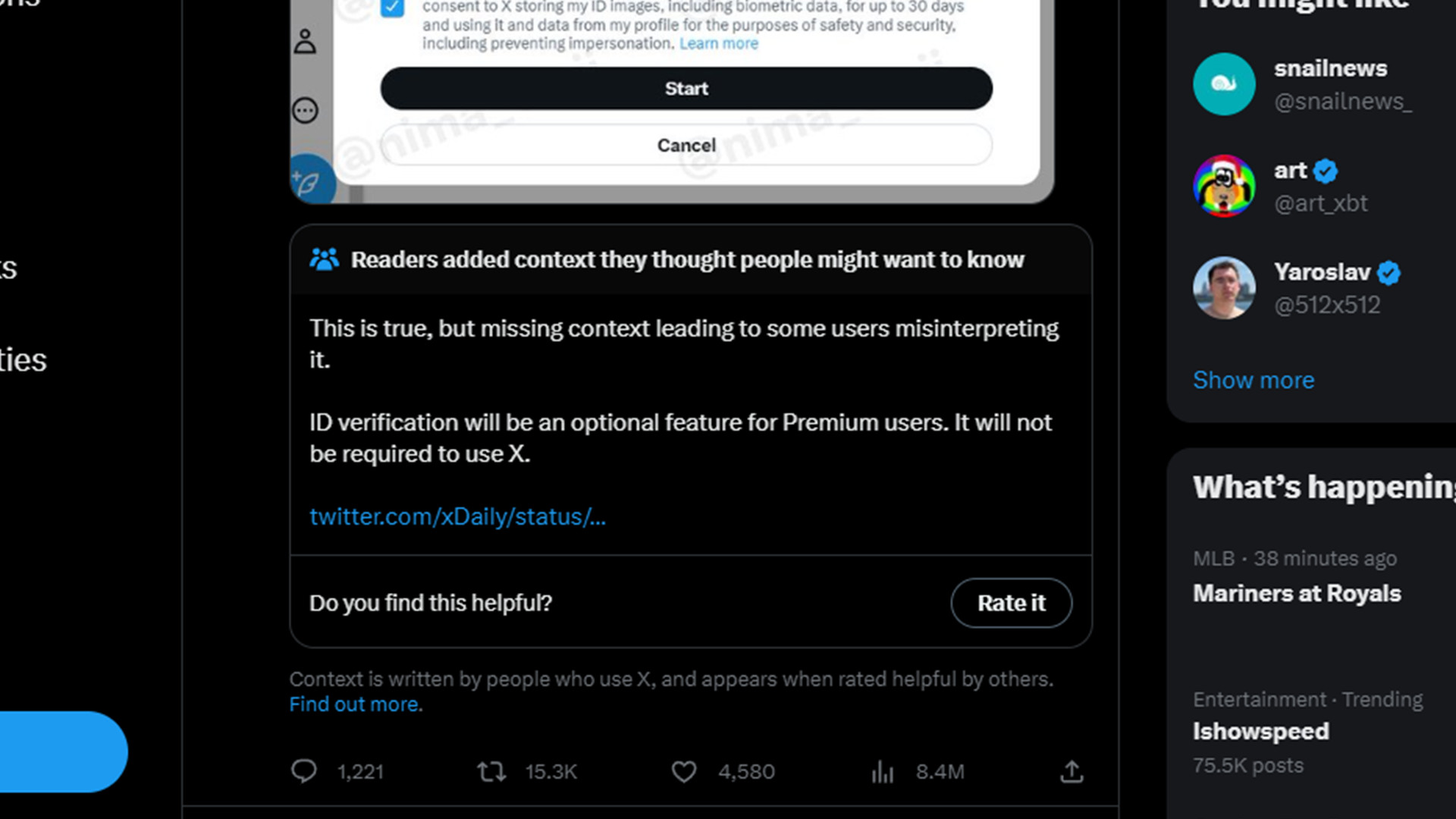
A launch date is unknown. It is worth mentioning that X’s Community Notes once claimed ID verification is almost here, but Owji’s may have missed some important context. The feature will actually be optional for Premium users. It won’t be a required security check for everyone.
However, during the writing of this article, those same Community Notes were altered to now say X is currently making no statements regarding "site-wide photo ID verification." The image below is the original statement.
Analysis: Just another sticker
The reason why this is being implemented, according to the fine print, is to combat impersonation on X. If you recall, Musk got rid of Twitter’s old verification system to then implement one where all you had to do was pay $8 to get a verified checkmark. This proved to be a disaster as the website soon became filled with fake accounts. Infamously, someone impersonated pharmaceutical company Eli Lily and then proceeded to tweet the corporation was making insulin free of charge. Eli Lily reportedly pulled all of its ads from Twitter, costing the social media platform millions.
The million-dollar question now is will this effectively stop X impersonators? We doubt it. It’s not like anything is really changing. It’s still $8 for verification, optional or not. Even if it was mandatory, would people be okay with giving their biometric data to Musk or some security company they never heard of? The sycophants probably, but that’s not most people.
It may still be just another worthless sticker to add to the collection.
Comments